Management Guidelines for Major Topics
Information Security Management
| Item | Explanation |
|---|---|
| Information Security Management | |
| Information Security Management |
Advantech recognizes that information security issues are critical to the Company's operational stability, product safety, and brand value as a global leader in the IoT industry. These factors are critical for stakeholders such as employees, customers, and investors. Furthermore, the FSC also amended regulations to mandate information security requirements for TWSE / TPEx listed companies. In the event of a major information security incident, they are required to publicly disclose material information. |
| Management Strategy | |
| Management Strategy |
The National Institute of Standards and Technology's (NIST) Cyber Security Framework (CSF) serves as the foundation for the Company's information security management strategy. The framework has five main functions: |
| Policy or commitment | |
| Policy or commitment |
To safeguard Company and customer interests, we are dedicated to upholding information security, continuously evaluating the efficacy of information security management, and minimizing the frequency of information security incidents. |
| Positive impact | |
| Positive impact |
Recognizing the increasing importance of the positive impact of information security and supply chain information security in the technology industry, the Company's efforts in fortifying information security can raise customer confidence, enhance overall corporate risk management, and enhance resilience against operational risks. |
| Negative impact | |
| Negative impact |
Information security breaches can negatively impact business operations by leading to the breach of confidential information, system service disruptions, reputational damage, customer loss, and increased legal risks for the Company.
|
| 2024 target achievement overview | |
| 2024 target achievement overview |
|
| 2025 Goals | |
| 2025 Goals |
|
| 2030 Goals | |
| 2030 Goals |
|
| Key action plans or programs in 2024 | |
| Key action plans or programs in 2024 |
|
| Effectiveness assessment | |
| Effectiveness assessment |
|
| Stakeholders impacted by the material topic and actions implemented by Advantech | |
| Stakeholders impacted by the material topic and actions implemented by Advantech |
|
Information Security Policy and Organization
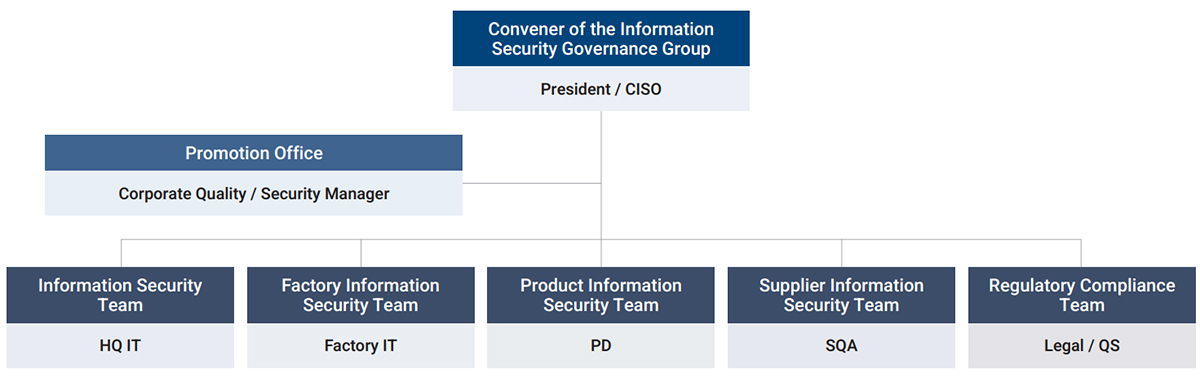
To safeguard the interests of Advantech and customers, we are dedicated to upholding information security, continuously monitoring information security management performance, and minimizing the frequency of information security incidents. To demonstrate the Company's commitment to information security, Advantech has appointed the President as Chief Information Security Officer (CISO). A crossdepartmental Information Security Governance Team has been formed, led by the Quality Control and Information Security teams. This team is in charge of promoting information security in various areas including computer information systems, physical environments, product security, supply chain management, and regulatory compliance. The Information Security Governance Team convenes a meeting every six months to review the management effectiveness, information security-related issues and directions. The Company also regularly reports the implementation status to the Risk Management Committee to integrate information security into the organization's risk management.
Organization Structure of Information Security Team
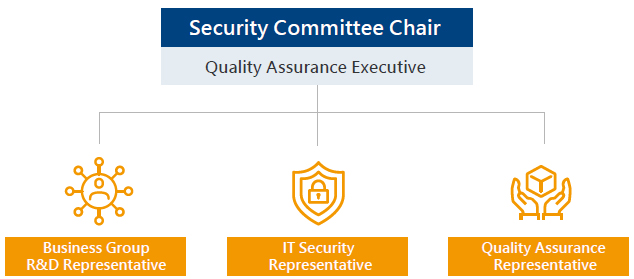
Furthermore, to enhance the management of product-related security issues, the Company established a Security Committee in October 2024. The Committee is composed of representatives from the R&D departments of various business units, IT and cyber security, Quality Assurance, and other relevant functions, with the executive of the QA unit serving as Chairperson. The Committee convenes regularly to address matters related to the Company’s products, including regulatory compliance, vulnerability management, development processes, and overall governance.
Advantech obtained "Information Security Management System (ISMS) ISO/IEC 27001:2013" certification in 2019 and has continuously maintained the validity of the ISO/IEC 27001 certificate. In 2024, headquarters IT server room management and backbone network, as well as Linkou plant OT operations, achieved certification to the ISO/IEC 27001:2022 standard. By following the management framework and control requirements of international standards across the four dimensions of strategy, management, technology, and awareness, the Company continues to improve the depth and scope of its information security governance.
Information and Cyber Security Management Strategy
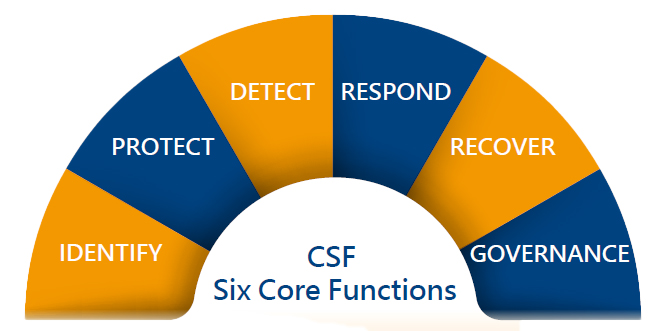
The National Institute of Standards and Technology's (NIST) Cybersecurity Framework (CSF) serves as the foundation for the Company's information security development roadmap. The framework has six main functions:
Identification, protection, detection, response, recovery and governance primarily refer to the measures that need to be managed or adopted at each stage of a company being attacked: before the incident (identification and protection), during the incident (detection and response), and after the incident (recovery).
In response to the United States Securities and Exchange Commission (SEC)'s rules governing cyber security risk management, governance, and disclosure of related events for Listed Companies, the Company has policies and relevant procedures for cyber security risk assessments; also supervise the cyber security risks of third-party service providers, and has contingency procedures and cyberattack recovery plans in place for cyber security incidents.
Furthermore, the Company actively participates in information security information-sharing organizations such as the Taiwan Chief Information Security Officer Alliance (CISO Alliance) and the Taiwan Computer Emergency Response Team / Coordination Center (TWCERT/CC) to obtain early warnings, threat intelligence, and vulnerability information related to information security. In collaboration with external security vendors and expert resources, the Company continues to monitors the latest trends, technologies, and developments in the field to strengthen its defense structure and measures, thereby effectively mitigating emerging threats.
In addition, the Company constantly assesses internal and external information security risks and trends to formulate corresponding information security management strategies accordingly. The current strategy focuses on reducing the attack surface, improving the visibility of information security risks, enhancing information security governance and risk awareness, as well as strengthening information security resilience. The information security-related action plans and key work achievements for 2024 are explained below.
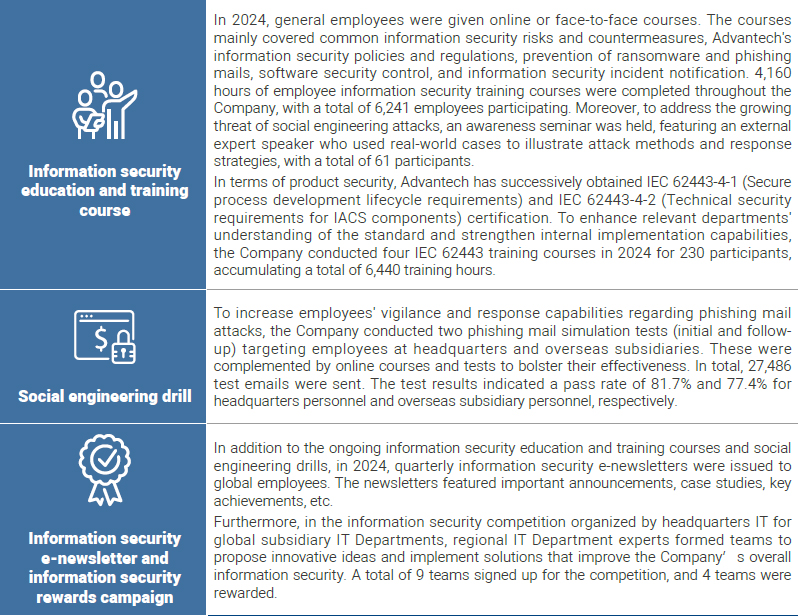
Reinforce employees' information security awareness
To enhance employees' awareness of information and cyber security, we have included information security as an annual compulsory course, providing e-Learning courses and online tests. In response to the increasing frequency of phishing email attacks, our company conducts social engineering drills to simulate phishing emails from hackers, testing employees’ awareness of information security risks. Additionally, we release a security newsletter every quarter. This newsletter includes updates on the latest information security trends, significant domestic and international cybersecurity incidents, important announcements, and more. These efforts are aimed at enhancing awareness and vigilance among our staff regarding information security.
Business continuity management (BCM) and disaster recovery drill
Considering that information services may be impacted by internal or external disasters or human error, Advantech planned for a remote disaster recovery mechanism utilizing the Linkou plant, with Neihu and Linkou locations serving as mutual remote disaster recovery and remote data backup locations. Advantech's IT department completed a disaster recovery drill for critical network and system services this year, with all aspects of the exercise completed within the Recovery Time Objective (RTO), validating the effectiveness of the framework and system for disaster response.
In response to potential operational disruptions at the plant due to disasters, the Company's Linkou plant conducted a BCM plan drill this year, using fire as the scenario. During the drill, relevant response plans and actions were executed according to emergency response levels and chronological order. The drill included simulating the notification of external fire departments for disaster relief assistance.
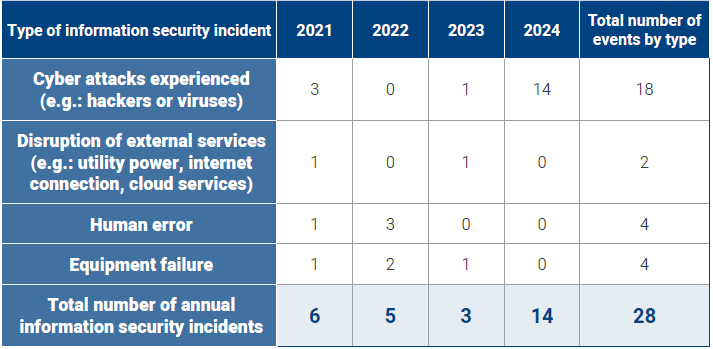
Status of Information Security Incidents in the Last Four Years
From 2021 to 2024, the company has not experienced any critical information security incidents, the number of information leakage incidents is 0, and there is no impact on customer rights or employee personal information due to information leakage. We experienced 14 cyber attacks this year; however, none had a significant impact on our operations. Of these, 12 were phishing mails, and two were suspected to be attacks by hackers or malicious software. After identifying the causes of the incidents, particularly those involving computer viruses, the IT department not only continued to fine-tune and enhance the performance of endpoint protection and antivirus tools, but also bolstered employee awareness campaigns on phishing mail prevention to increase their vigilance through social engineering drills.